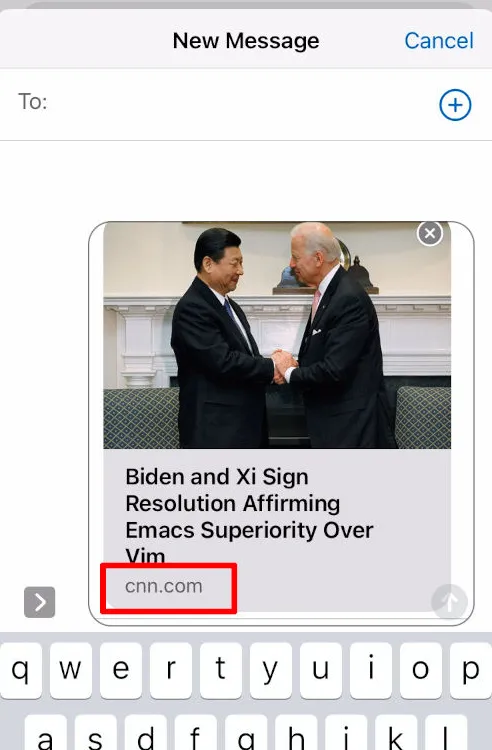

It's April 2023, and today you'll learn who among your circle clicks beyond headlines: we'll forge arbitrary, entirely functional iMessage link previews – e.g., from CNN – by serving a victim device four html tags.
This consists purely of misuse as opposed to any kind of exploitation. It does however raise questions as to how we should handle opengraph and similar standards going forwards. I'm picking on iMessage because it's the worst offender I identified during some poking around.
In short, we're serving bad content from an iOS device visiting an attacker-controlled webpage. Receiving iOS devices trust the bad content by default. This example uses a bridged VM accessible on your LAN, but hypothetically any page you can 1) hit from your attacker iOS device and 2) exercise control over will work.
My env:
boot the VM with the live ISO - make sure to select bridged networking so the guest is assigned a distinct IP
open a shell in the VM and install apache2:
sudo apt update && sudo apt install -y apache2
overwrite the apache default landing page with a crafted, minimal set of OpenGraph tags. For the example above I overwrote the file at /var/www/html/index.html with content:
<!DOCTYPE html>
<html>
<head>
<meta property="og:type" content="article" />
<meta property="og:title" content="Biden and Xi Sign Resolution Affirming Emacs Superiority Over Vim" />
<meta property="og:url" content="https://cnn.com" />
<meta property="og:image" content="https://www.politico.com/dims4/default/673ad23/2147483647/legacy_thumbnail/1200x799%3E/quality/90/?url=https%3A%2F%2Fstatic.politico.com%2F1e%2Fe9%2F22e718ad4cd2b2ffbdbb9c7c44e1%2F211112-joe-biden-xi-jinping-getty-773.png" />
</head>
</html>
og:title This is title of the content the recipient will receiveog:type I've only used articles. Unknown how other choices affect behaviorog:url This is the source site the user will see, and where they'll land if they click through. The LAN IP address is replaced with this urlog:image A direct link to some desired preview image. I used a random shot from googleon your iOS device, navigate to the IP address of the bridged VM
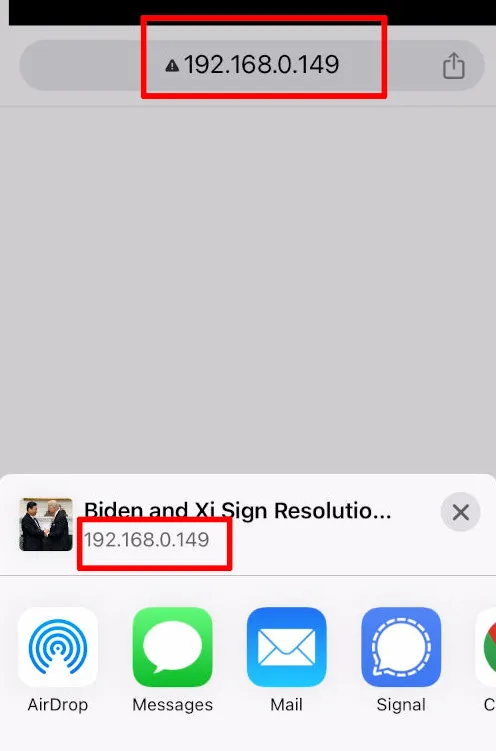
sharing the page with iMessage recipients results in the crafted content preview
When the page is hosted on your LAN, devices not on the LAN cannot re-share the content. I haven't tested other network architectures, e.g., hosting a remote attacker-controlled page available to both sender and recipient
The approach (LAN-local, minimal OpenGraph tag set) outlined above only works with iMessage. I could not replicate the behavior with WhatsApp or Signal